
Standard Operating Procedure / SOC
Continuous Monitoring – Incident Response Process
Detection (SIEM)
The SIEM:
-
- collects logs from on-site collector
- classifies the event type and parses the event attributes
- performs data enrichment (DNS resolution, GEOIP, etc)
- processes the logs through correlation rules, which look for known patterns and threat indicators
- generates incidents for events that match the correlation rules
- generates tickets for related invidents
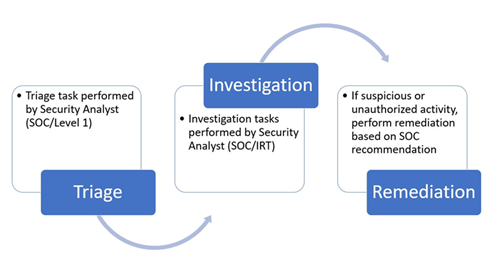
Triage
The Level 1 Security Analyst:
-
- receives and reviews the ticket
- checks the ticket against account notes and exceptions
- checks the ticket against known signs of a false positive
- escalates the ticket to IRT investigation, if not closed in the previous two steps
Investigation
The IRT Security Analyst:
-
- references the SOP for the triggering correlation rule
- reviews the incident attributes and raw event logs for additional information
- investigates the source/destination via WHOIS records, geolocation information, and numerous threat intelligence feeds
- checks for other related internal incidents (incidents used for investigation which do not trigger tickets)
- searches archived logs for related events
- investigates the specific threat for relevant information (affected devices/versions, signs of attack, remediation steps), etc
- compiles all relevant information and escalated the ticket to remediation
Remediation
The Remediation Team:
-
- verifies the reported activity is suspicious or unauthorized
- perform remediation based on Security Operations Center recommendations
